Podcast Episodes
Back to Search
EP 271.5 Deep Dive. Santa and The IT Privacy and Security Weekly update for the week ending December 23rd., 2025
Season 6 Episode 271
Our daily digital tools—browsers, apps, and smart devices—offer convenience but also expose us to hidden security risks. This guide reveals how ordinary technologies can imperil privacy and safety, f…
Published on 15 hours ago

Santa and The IT Privacy and Security Weekly update for the week ending December 23rd., 2025
Season 6 Episode 271
EP 271. For this week’s holiday update:
Santa’s naughty list exposed in data breach. A lighthearted reminder from a past holiday hoax: even Santa's list isn't immune to data breaches.
How China Built …
Published on 2 days ago
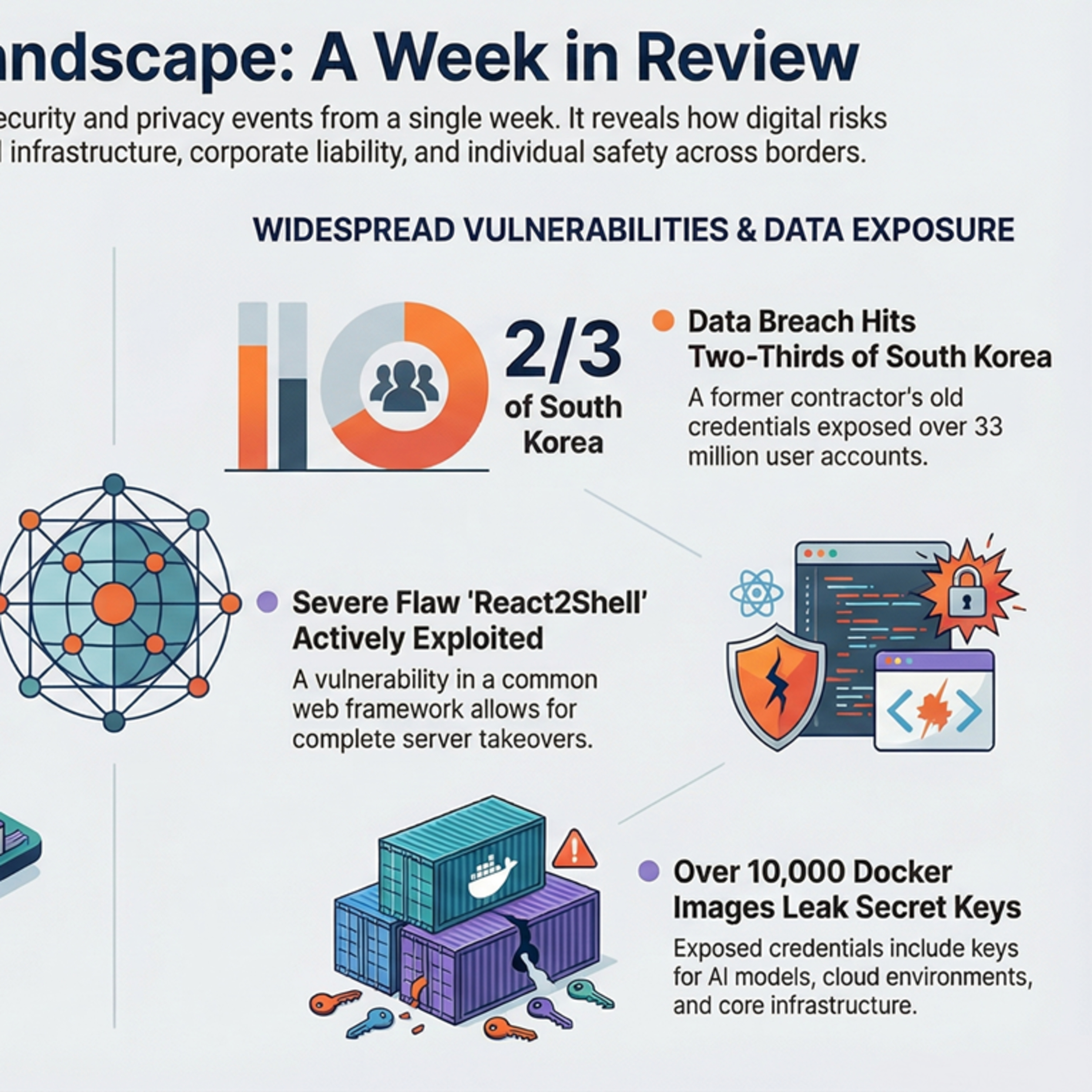
EP-270.5 Deep Dive. Honey Don't. The IT Privacy and Security Weekly update for the week ending December 16th., 2025
Season 6 Episode 270
Global: Over 10,000 Docker Hub Images Found Leaking Credentials, Auth Keys
The widespread exposure of sensitive keys in Docker images underscores the dangers of embedding secrets in container builds. …
Published on 1 week ago

Honey Don't. The IT Privacy and Security Weekly update for the week ending December 16th., 2025
Season 6 Episode 270
EP 270.
In this week’s update:Security researchers uncover over 10,000 publicly available Docker Hub images exposing sensitive credentials and API keys, posing severe risks to production systems and …
Published on 1 week, 2 days ago

EP 269.5 Deep Dive. Truckin' With the IT Privacy and Security Weekly update for the week ending December 2nd., 2025
Season 6 Episode 269
Modern security is defined less by a single network perimeter and more by a web of interconnected partners, vendors, and shared infrastructure, where one weak link can trigger widespread impact. Crim…
Published on 3 weeks ago

Truckin' With the IT Privacy and Security Weekly update for the week ending December 2nd., 2025
Season 6 Episode 269
EP 269. In this week’s update:Organized crime syndicates are now recruiting skilled hackers to orchestrate sophisticated digital hijackings of entire truckloads of high-value cargo.A bizarre Windows …
Published on 3 weeks, 2 days ago

EP 268.5 Deep Dive. Chew Thoroughly. The IT Privacy and Security Weekly Update for the week ending November 25th., 2025
Season 6 Episode 268
The EPA approved two new PFAS-containing pesticides for food crops and plans four more. Scientists warn this deliberately increases dietaryexposure to persistent chemicals linked to cancer and birth …
Published on 4 weeks ago

Chew Thoroughly. The IT Privacy and Security Weekly Update for the week ending November 25th., 2025
Season 6 Episode 268
EP 268
The US Environmental Protection Agency (EPA) approves PFAS-containing pesticides for everyday food crops, opening a new pathway for “forever chemicals” to reach dinner plates.
A magician who im…
Published on 1 month ago

EP 267.5 Deep Dive. A Wrench in the IT Privacy and Security Weekly Update for November 18th., 2025
Season 6 Episode 267
This week's security landscape is defined by three converging vectors: the expansion of threats into physical and environmental domains, persistent vulnerabilities in core digital infrastructure, and…
Published on 1 month ago

A Wrench in the IT Privacy and Security Weekly Update for November 18th., 2025
Season 6 Episode 267
EP 267
In this week’s update:
Wealthy Bitcoin holders in Switzerland are now learning to bite through zip ties as 'wrench attacks' shift crypto threats from cyberspace to real-world violence.Iceland h…Published on 1 month, 1 week ago