Podcast Episode Details
Back to Podcast Episodes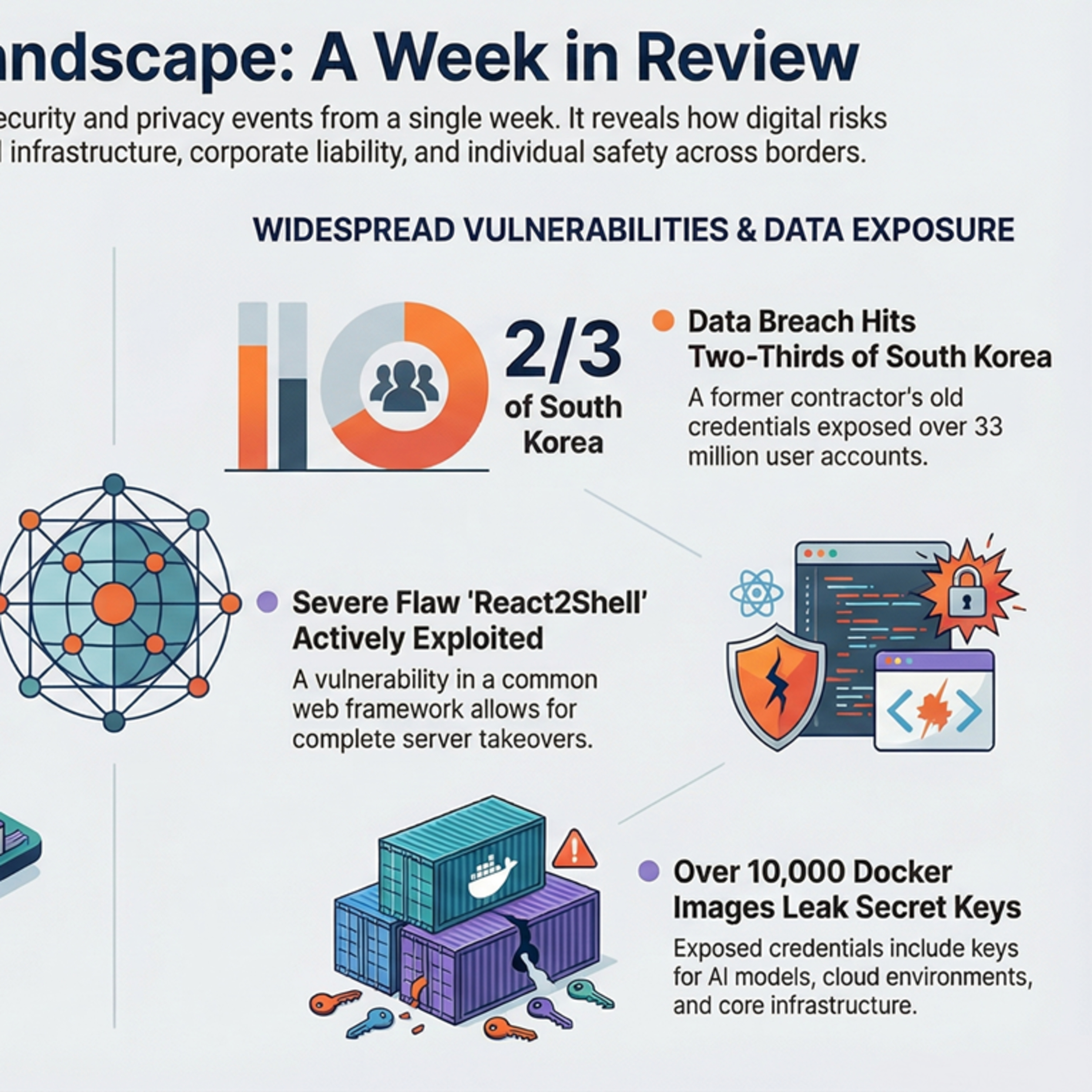
EP-270.5 Deep Dive. Honey Don't. The IT Privacy and Security Weekly update for the week ending December 16th., 2025
Season 6 Episode 270
Global: Over 10,000 Docker Hub Images Found Leaking Credentials, Auth Keys
The widespread exposure of sensitive keys in Docker images underscores the dangers of embedding secrets in container builds. Developers should prioritize centralized secrets management and routine scanning to prevent lasting breaches even after quick fixes.
CN: Chinese Whistleblower Living In US Is Being Hunted By Beijing With US Tech
This case highlights how advanced surveillance tools can erase borders, enabling persistent transnational repression. It serves as a stark reminder that personal data, once captured, can fuel harassment far beyond its intended use.
EU: 193 Cybercrims Arrested, Accused of Plotting 'Violence-As-a-Service'
The successful disruption of "violence-as-a-service" networks shows that coordinated law enforcement can counter the dangerous blend of online recruitment and offline crime. Continued vigilance is essential to protect communities from these evolving hybrid threats.
Global: Google will shut down “unhelpful” dark web monitoring tool
Google's decision to retire its dark web monitoring feature reflects the challenge of turning breach notifications into truly actionable advice. Users should seek security tools that not only alert but also guide clear, practical steps for protection.
Global: Second JavaScript Exploit in Four Months Exposes Crypto Sites to Wallet Drainers
Repeated supply-chain vulnerabilities in core JavaScript libraries reveal how quickly dependencies can become attack vectors. Maintaining rigorous patch management and dependency monitoring is now as critical as safeguarding cryptocurrency itself.
RU: All of Russia’s Porsches Were Bricked By a Mysterious Satellite Outage
The mass immobilization of connected vehicles illustrates the hidden risks of over-reliance on remote satellite systems for essential functions. As cars grow smarter, resilience against connectivity failures must become a design priority.
RU: Russian Hackers Debut Simple Ransomware Service, But Store Keys In Plain Text
Even motivated threat actors can sabotage their own operations through basic security oversights like hardcoding keys. This flaw reminds defenders that attacker mistakes can offer unexpected opportunities for recovery without payment.
US: More Than 200 Environmental Groups Demand Halt To New US Datacenters
The growing backlash against unchecked data center expansion ties AI progress directly to real-world strains on energy, water, and household bills. Balancing technological advancement with sustainable infrastructure is no longer optional but urgent for communities nationwide.
Published on 1 week ago